
Cyber-Security
World's 1st Unique Patented Security Data Lake
100% Monitoring of 100% Transactions in Real Time
Equals 100% SECURITY
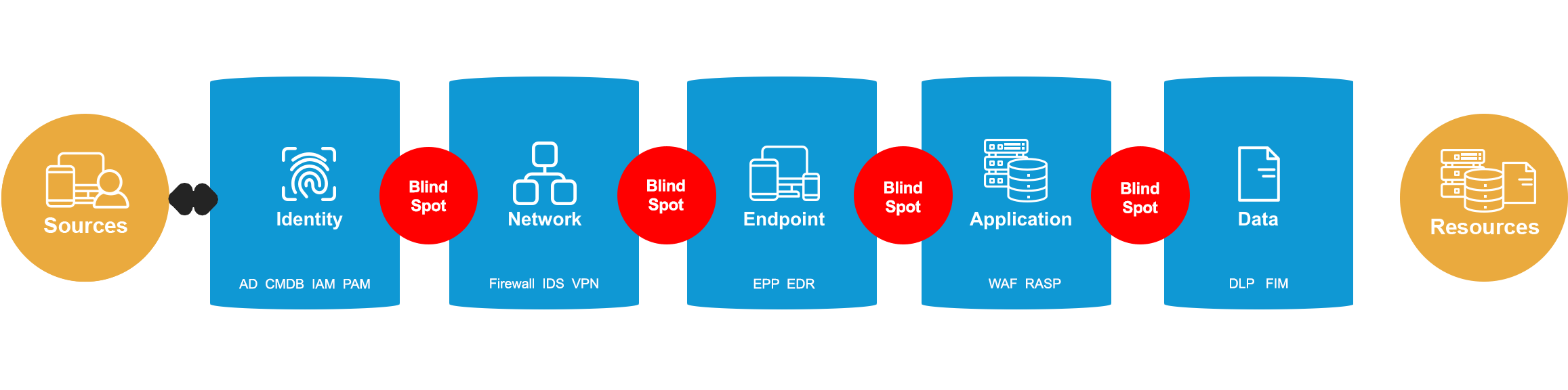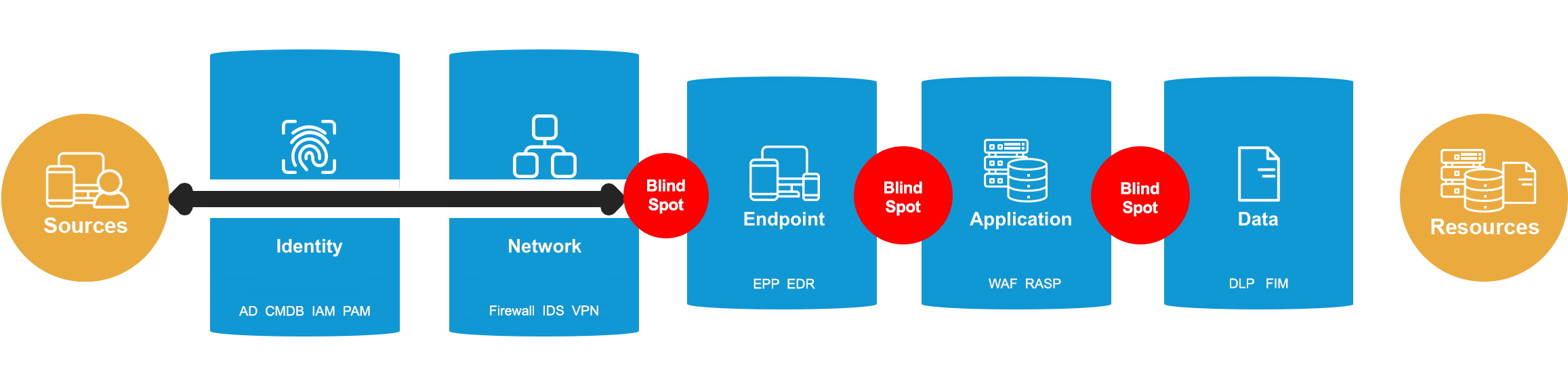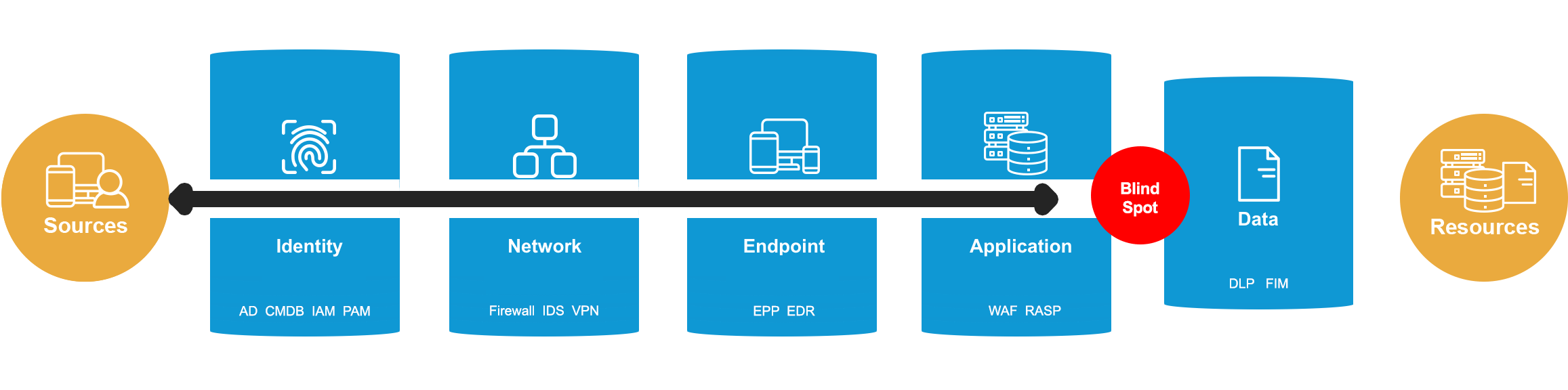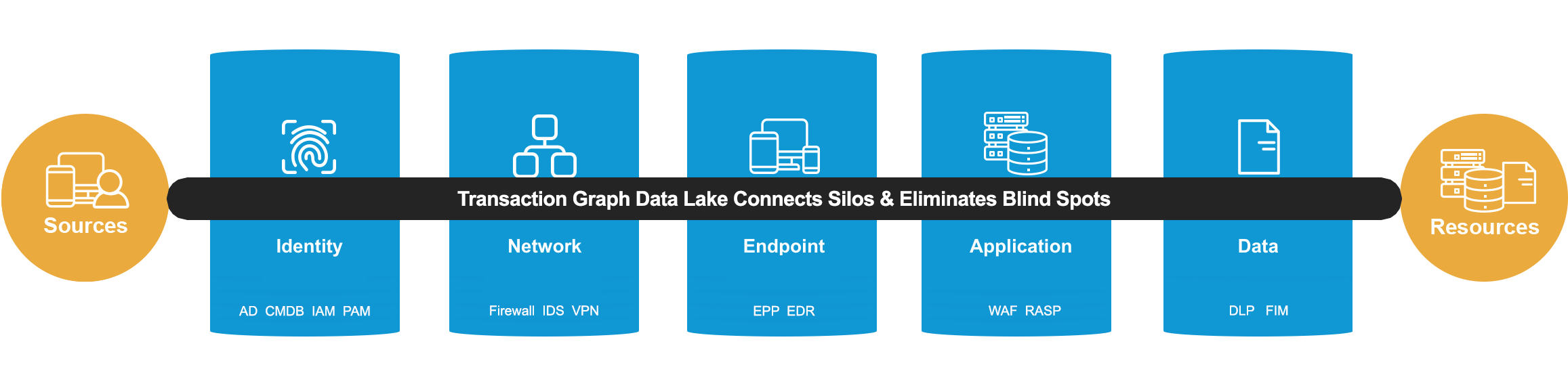
The First Purpose-Built Data Lake for Security
Simplify the security stack
Enforce NIST controls
Detect MITRE tactics
Active Cyber Risk Management Powered by The First Purpose-Built Security Data Lake
Prismo Transaction Graph is the first data lake purpose-built for security at enterprise scale, providing Active Cyber Risk Management and enabling enterprises to protect IT infrastructure and applications while simplifying the security stack and reducing costs.
Active Cyber Risk Management
A purpose-built security data lake provides unprecedented visibility and control. Integrated risk management for governance and operations
Continuous risk assessment
Event-driven discovery of users, assets and transactions. Assess risk and expose blind spots. Highlight configuration drift in CMDB, AD, DNS
Minimize attack surface
Combine real-time activity with configuration to discover risks and enforce controls. Discover vulnerabilities using CVE and Microsoft KB. Delete unused accounts. Policies protect until patched
Excess privileges and misconfiguration
Validate user identity with local accounts to halt lateral movement. Identify outlier behavior for users, networks and data access to detect human oversight and errors.
Prevent Malware from installing
Provenance policies block advanced Malware, including Ransomware, at install.
Assure NIST compliance with NextGen GRC
Map controls to NIST framework. Risk Registry, persona specific active dashboards for C-suite, architects and analysts. Detailed 3 to 7-year audit trail in the data lake.
Lockdown Servers & Workloads
Defend critical applications, tools and workflows against software supply chain attacks. Secure enterprise crown jewels located on-premise and in public clouds running Linux, Windows or Containers across the entire server lifecycle.
Certified Provisioning
Validate golden image with CIS hardened configuration. Authorize software installs, updates and patches from sanctioned channels. Return server to versioned state. Provenance policies automatically block unsanctioned executables at install.
Integrity of Operations
Discover and fingerprint scripts, tools and workflows. Detect and block backdoors and other compromises in trusted channels. Bubble wrap servers and workloads until they are patched.
Least-Privilege during Maintenance
No standing access to production. Just-in-Time certificates for break glass. Rich transaction context and granular control of admins and DevOps.
Micro-Segment Execution
Continuous discovery and profiling auto-segments network and system behaviours.
Minimize human error via Intent-based policies, recommendation engine, what-if and dry-run.

See how active risk management can help your organisation
Let's Talk




Improved ROI
Secure transformation
Simplified security stack
Seemless insertion
Auotmated operations
NextGenCRG
Quantify exposure
Prioritize security spend
Assure NIST Compliance
Efficient Audits
Precise Control
Reduce the attack surface
Easty to use intent policies
Conform to MITRE tactics
Model-based automation
Efficient Response
Slash false positives
Prioritize Threats
1-click response
Threat hunting toolkit
CIO/CFO
CISO/CRO
Architect
Analyst
Cyber Risk Management is built for all security stakeholders


2.png)
